This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
The News: In early March, the Biden-Harris Administration announced the National Cybersecurity Strategy, developed to provide a safe, secure ecosystem for all Americans. Find the Fact Sheet on the announcement here.
The National Cybersecurity Strategy Proposed by the Biden-Harris Administration Portends Greater Scrutiny for IT Operations
Analyst Take: The proposed National Cybersecurity Strategy recently announced by the Biden-Harris administration represents some significant changes, and heightened scrutiny for IT operations. With the rise of data extortion, data destruction, sophisticated and innovative ransomware attacks, and state-sponsored cyber-attacks, the cyber threat landscape is extensive and diverse. With the release of this new national cybersecurity strategy, activity by cyber threat actors is elevated to the level of a national security threat.
What are the Key Takeaways for IT Operations?
While a specific implementation plan for the national cybersecurity strategy is still in progress, due to be released over the next couple of months, I see there are some immediate takeaways for IT Operations with the unveiling of the strategy. Arguably the most significant change I see ahead is that best efforts measures, which have heretofore been the norm, are no longer sufficient for cyber resiliency. Specifically, the plan proposed by the national cybersecurity strategy portends the implementation of minimum standards for IT infrastructure availability, resiliency, and security, that organizations in private industry will have to comply with.
The plan further amplifies the need for an IT infrastructure strategy that leads with cyber resiliency and is governed by intentional, coordinated, and vetted policy, across industries as a whole.
Beyond driving policy, a key part of the national cybersecurity strategy is that federal agencies will also be setting examples for best practices. For example, federal incident response plans will be vetted and organized, and IT systems will be modernized. This modernization will include a focus on adopting a zero-trust architecture, which goes beyond more traditional network perimeter security measures to include strict access control (e.g., multi-factor authentication), end-to-end encryption, and visibility into the attack surface. Additional detail is available in the Cybersecurity and Infrastructure Security Agency’s (CISA) published reference architecture.
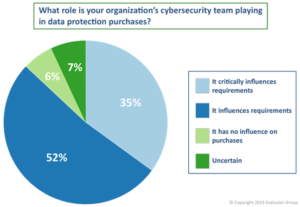
The good news for IT Operations teams? The need for cyber resiliency will drive investments in IT solutions. According to Evaluator Group’s Trends in Enterprise Data Protection study, cybersecurity teams influence data protection purchase requirements for more than 50% of enterprises, and budget for new data protection-related purchases will come from the security team for more than one-third of enterprises.
Although I generally see the launch of a National Cybersecurity Strategy designed to provide increased protections as a good thing, especially for companies that provide security-based IT solutions, as with most situations, the adage caveat emptor (buyer beware) still applies. IT tools and policies will receive increasing scrutiny, which will also go hand in hand with increased incentive, along with pressure to mitigate threats.
This is especially true as organizations become mandated to report security breaches, which could lead to expensive fines, reputational damage, and other negative repercussions. Greater communication and collaboration between IT and key business stakeholders on data privacy and protection service level requirements become even more critical — which I view as a good thing overall. Moving forward, cybersecurity needs to be a boardroom-level conversation, not just an IT conversation, which benefits businesses, IT teams, and users alike.

